Rodrigo Duarte Favarini Silva
EC-Council University
ECCU 516 – The Hacker Mind: Profiling the IT Criminal!
Classifications of computer criminals
With the expansion and diversification of cybercrime, strategies have become an obstacle to understanding and categorizing crime agents (Sabillon, Cano, Cavaller Reye & Serra Ruiz, 2016). As cybercrime does not have a single definition in consensus with all researchers, the actors who commit the crimes also cannot be classified in a unique way (Sabillon et al., 2016). Stewart, Chapple and Gibson (2015) showed the three classic forms of hacking classification such as Black-Hats, Gray-Hats and White-Hats. This classification is more related to their ethical actions, and it is not understood as a criminal classification:
- Black-Hat: Hackers with excellent computing skills that are attracted to malicious activities. Their motives are to cause damage, steal information, destroy data and earn Money (Sabillon et al., 2016).
- Gray-Hat: Hackers that work both offensively and defensively at different situations depending on their own interest or purpose (Sabillon et al., 2016).
- White-Hat: Individuals with hacking skills acting to protect networks. They work in corporate environments as security analysts (Sabillon et al., 2016).
Some authors have written about the taxonomy of cybercriminals and have developed studies based on their actions and level of knowledge (Bosworth, Kabay & Whyne 2004). The first studies in this regard were conducted by Nicholas Chantler and published in 1995, splitting hackers in Lammers, Nephites and Elite. This classification became widely known and took into account the technical skill of the actor (Zhang, Tsang, Yue & Chau, 2015).
Lammers are low technical skill criminals, primary motivated by revenge and engaged in their illegal activities for the shortest time. 10% of the cybercriminals are in this category (Bosworth, Kabay & Whyne, 2004). Neophytes are more mature than Lammers and have consolidated computer knowledge, allowing them to increase the illegal actions. 60% of cybercriminals are neophytes (Bosworth et al., 2004). Elite is a group with the highest level of computer knowledge and computer crime. Motivated by the desire for knowledge and curiosity, they engage in illegal activities for the intellectual challenge. 30% of those agents are considered part of this group (Bosworth et al., 2004)
Rogers (2010) amplified the understanding of the classification of cybercriminals by reviewing his previous 2005 studies. He proposed a new perspective based on technical expertise, behaviours, motivation, and moral development. The motivational aspects presented in their stuccoes are revenge, financial, notoriety and curiosity. These aspects, combined with the skill level, can be associated by forming a circumplex model.
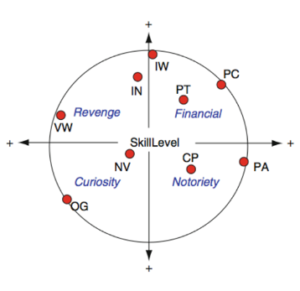
Figure 1: Robert’s model describing the nine categories of cybercriminals
Interpreting this model, Information Warriors (IW), Professional Criminals, Political Activists (PA), Old Guard Hackers (OG) and Virus Writers (VW) are the actors with the highest skill level. The notoriety of their acts drives Cyberpunks (CP) and Political Activists. Professional Criminals, Information Warriors and Petty Thieves (PT) guide their actions by financial objectives. Old Guard Hackers and Novices (NV) have the inner desire to learn and are driven by curiosity. In the last group, we have individuals moved by revenge. They are the Virus Writers and Internals (IN).
The categories shown by the authors are not exclusive to each other or even exact, which indicates that the motivation and objectives of the person who authored the crime are what classifies them at the moment of the crime. In this sense, what we can have as a difference between them is the level of knowledge of the individual, which ultimately also indicates how dangerous the cybercriminal is (Sabillon et al., 2016).
References
Bosworth, S., Kabay & Whyne, E. (2004). Computer security handbook. John Wiley & Sons.
Rogers, M. K. (2010). The Psyche of Cybercriminals: A Psycho-Social Perspective. Cybercrimes: A Multidisciplinary Analysis, 217-235. doi:10.1007/978-3-642-13547-7_14
Stewart, J. M., Chapple, M. & Gibson, D. (2015). CISSP (ISC)2 Certified Information Systems Security Professional official study guide. Indianapolis, IN. Sybex, a Wiley brand.
Sabillon, R., Cano, J., Cavaller Reyes, V. & Serra Ruiz, J. (2016). Cybercrime and Cybercriminals: A Comprehensive Study. International Journal of Computer Networks and Communications Security, 4(6), 165-176.
Zhang, X., Tsang, A., Yue, W. T., & Chau, M. (2015). The classification of hackers by knowledge exchange behaviors. Information Systems Frontiers, 17(6), 1239-1251. doi:10.1007/s10796-015-9567-0
